Challenge Description: We found ourselves locked in an escape room, with the clock ticking down and only one puzzle to solve. The final challenge involves opening the door, and the clue provided to use by the game master is that the key for the encrypted password is a 4-byte sequence.
Walkthrough
The challenge download gives us two files lock.vhd and out.txt.
The second file is presumably the output of the first, and contains two columns of values.
At first glance the first file appears to be a Virtual Hard Disk, but based on the name of the challenge and a quick search of the import use ieee.std_logic_1164.all, it can be determined that this is a VHDL file.
If you want to learn more about VHDL files, and how to write/read them, I recommend this playlist:
Your first VHDL Program.
The first part of this file is creating an xor_get function that takes 2 inputs, each 2 bytes wide, XOR’s them, and outputs the 2 byte result to output.
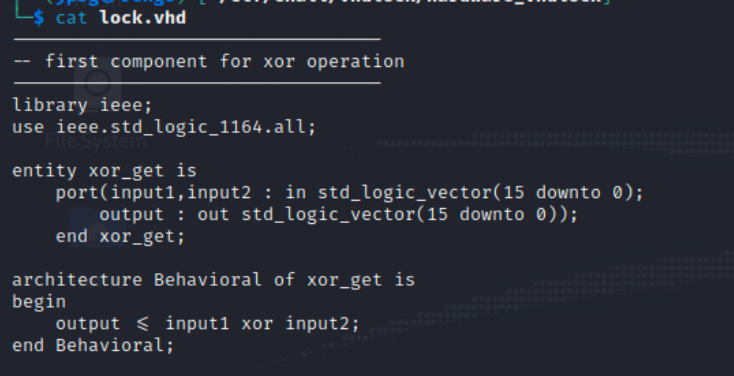
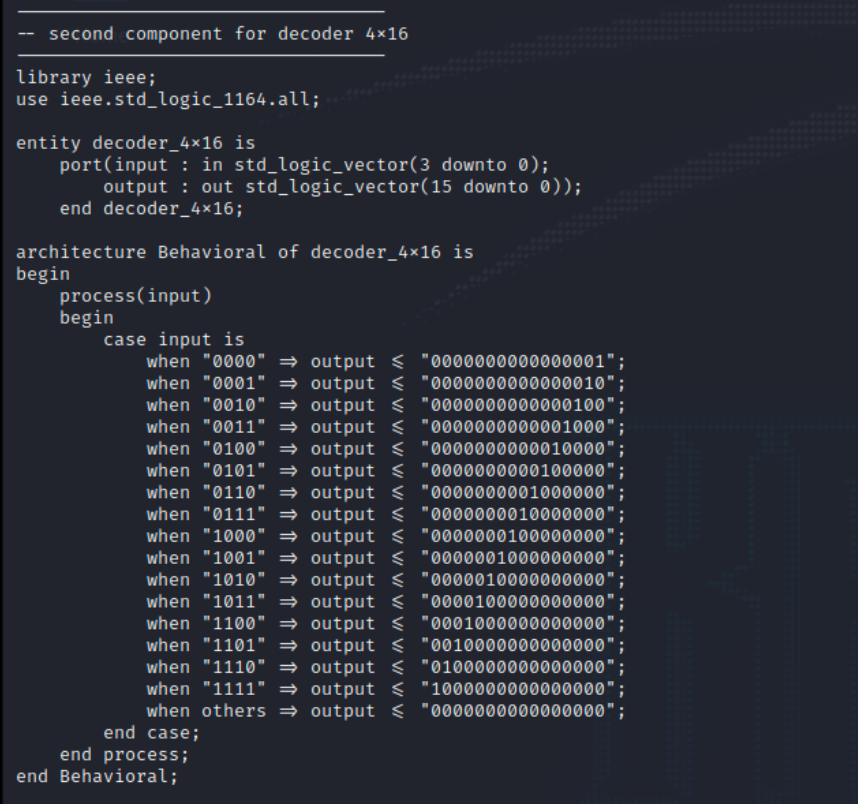
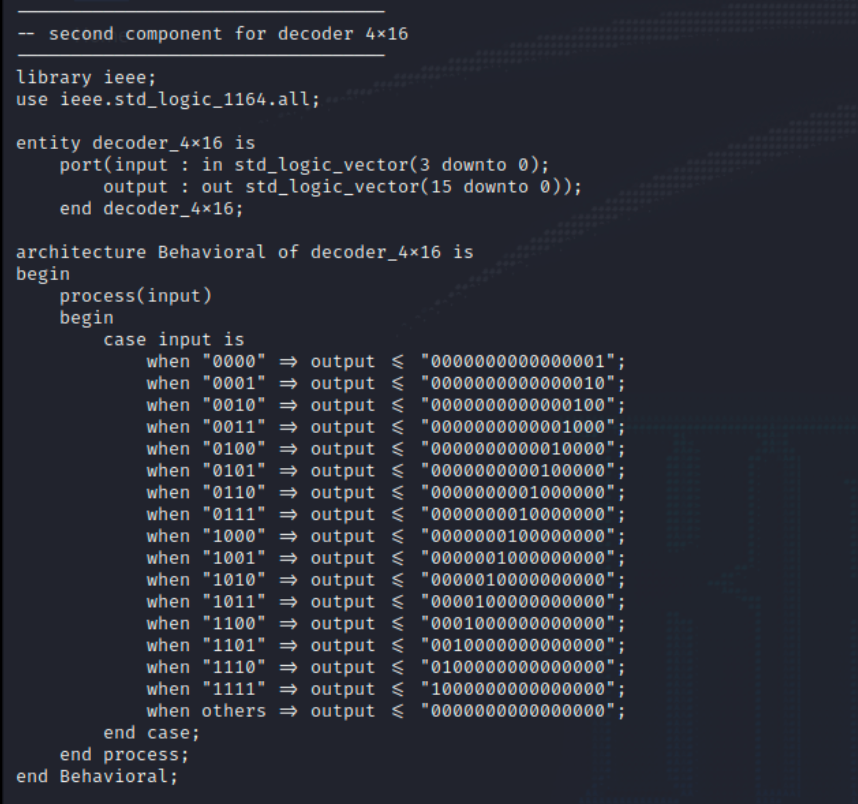
The second component takes in a 4 but value and maps it to a 16 bit value. This value is given to output.
The last component of the file is where the process of generating out.txt can be explained.
The main entity describes the inputs we can expect.
2 4-bit values, along with a 2 byte XOR key, and it will have 2 2-byte outputs, seen in out.txt.
Our 2 4-bit values are translated into a 16-bit value, and then those values are XOR’d against the unknown key.
However, given that HackTheBox flags always have the format HTB{...} we can assume to know the first 4 inputs.
Since we now know the 2 of the 3 values used in the XOR operation used to generate the outputs, we can derive the 4 byte key using the following process:
| |
Here is the code to generate the key:
| |
It will output the values:
| |
From this we know the key to be 0x33313137.
Now the rest of the challenge is just to reverse the outputs so we can figure out the inputs.
Here is the code to solve the challenge:
| |
The flag is: HTB{I_L0v3_VHDL_but_LOve_my_5w33thear7_m0re}.
