Challenge Description: While cleaning up the workspace of a recently retired employee, we noticed that one of the core files of the very important programs they were working on didn’t match up with the backups we have of it, could you check it out for us?
Initial Analysis
Upon running the executable, nothing out of the ordinary seemed to happen.
The .exe printed “Hello World!” and exited normally.
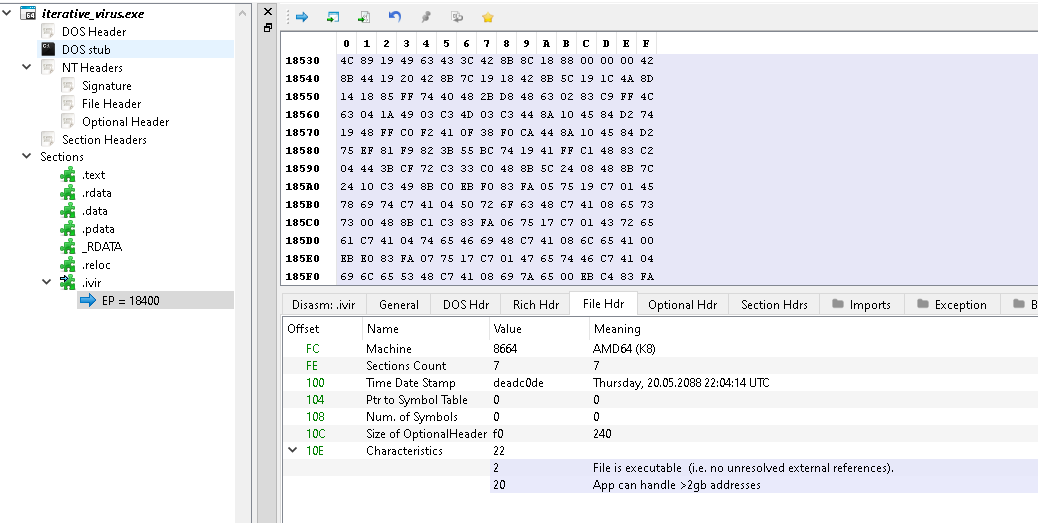
PEBear showed that there was another strange section in the exe file called .ivir.
I made the assumption that this was a reference to I terative VIRus, and the entry point being in this section further reinforced my theory that this was the “virus” part of the file.
The time stamp was set to deadc0de which was also strange, since that translates to a date well into the future.
Reversing with IDA Free
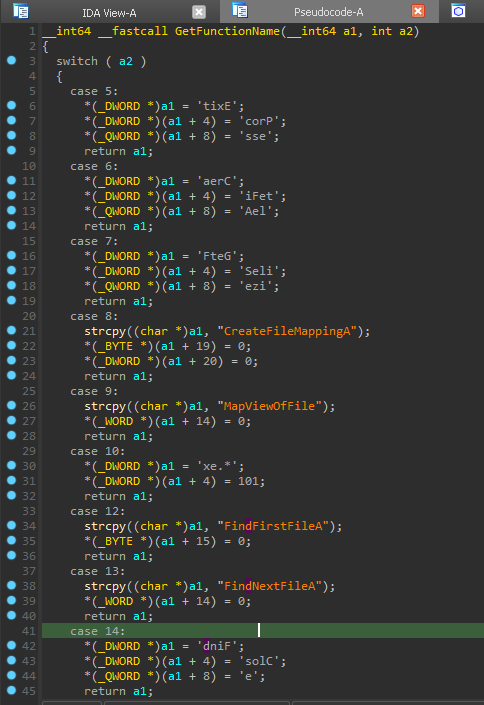
The first interesting function to look at is one that returns a function name based on a number it is given. It uses stack strings to prevent analysis tools from detecting the string as a string. We can right click on the hex values to convert them to characters. The result name is then passed to another function that seems to return a function pointer. This made me think that the exe was dynamically resolving functions.
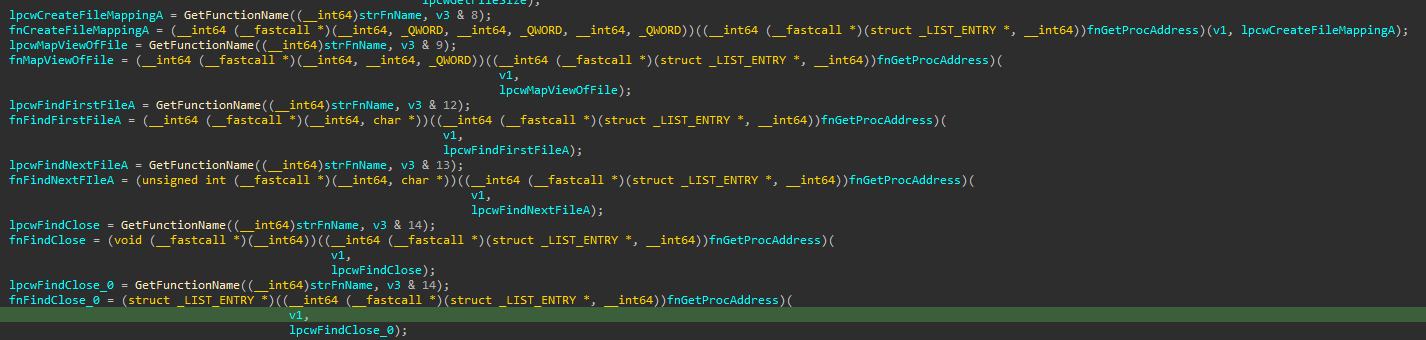
After we sort through each function call and match up the result, we can see the functions that have been resolved:
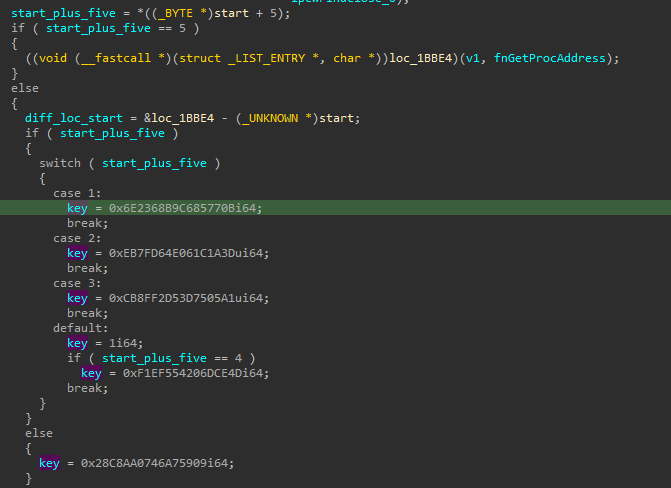
After these functions have been resolved, there is a value 5 bytes after the entry point that is compared. If the value is 5, then a function is called. However, this function seems to be broken, encrypted, or heavily obfuscated since the disassembly doesn’t seem valid. Otherwise, what seems like a key value is chosen and saved.
Then the exe will iterate over all the *.exe files in its current directory, confirm some checks, and if everything looks good it will perform some actions on the current .exe file.
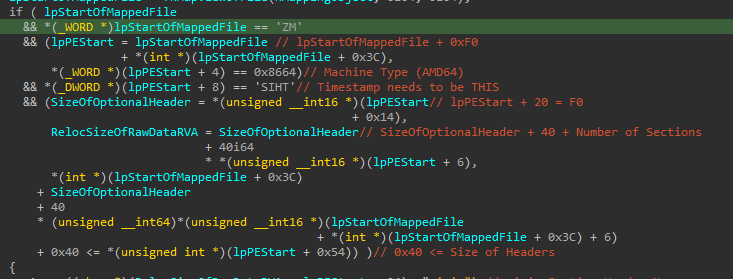
The main check is that the timestamp of the file needs to be set to THIS otherwise the infection of the file will not take place.
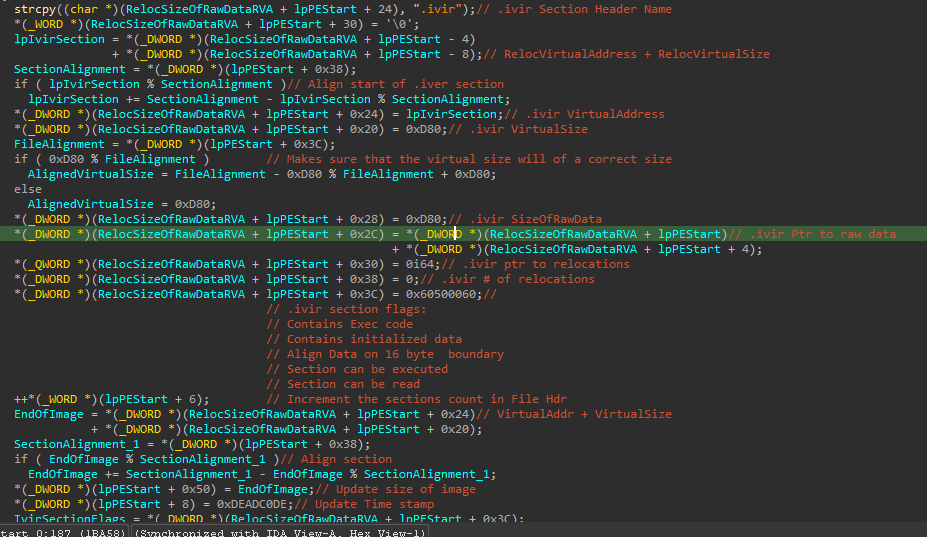
Most the proceeding infection process isn’t super important, and was in fact pretty tedious to look through and rename. A new section and section header are added and modified to make sure they adhere to alignment rules, and the rest of the process is just copying over the infection code and making it so it replaces the entry point of the victim file.
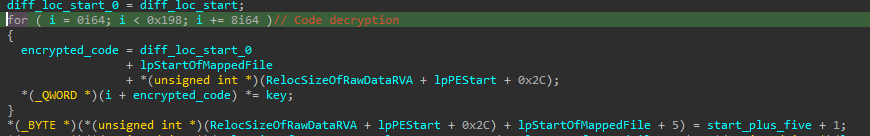
The end of the process loops over the data from the broken function from earlier, and multiplies it against the key value selected earlier.
This new modified code is then copied into the victim file.
Then the byte 5 bytes ahead of the entry point is incremented and copied into the victim file.
This means when the newly infected victim exe is run, it will use the second key.
Then the next file to be infected will use the third key, and so on until the 4th iteration when that special byte is set to 5.
At that point the strange function from earlier runs.
This implies that after a certain number of infections the strange function reveals itself.
I verified most of this with dynamic analysis as well, but didn’t take any screenshots.
If you want to verify with a debugger, set a breakpoint after the MapViewOfFile function and follow it in dump.
From there you can follow along with the exe code as it checks and modifies different parts of the victim file.
I ran the exe in x64Dbg, and copied out the encrypted code so I could manually decrypt it.
You could just manipulate the registers to do it all within x64Dbg but I ran into exceptions doing that so I opted for the python approach.
Here is the script that decrypts the flag function:
| |
Attempting to analyze this decrypted code didn’t yield any results, so I figured it required the context of the full program to work successfully.
At this point I used HxD to patch the virus exe to overwrite the encrypted code with the decrypted one.
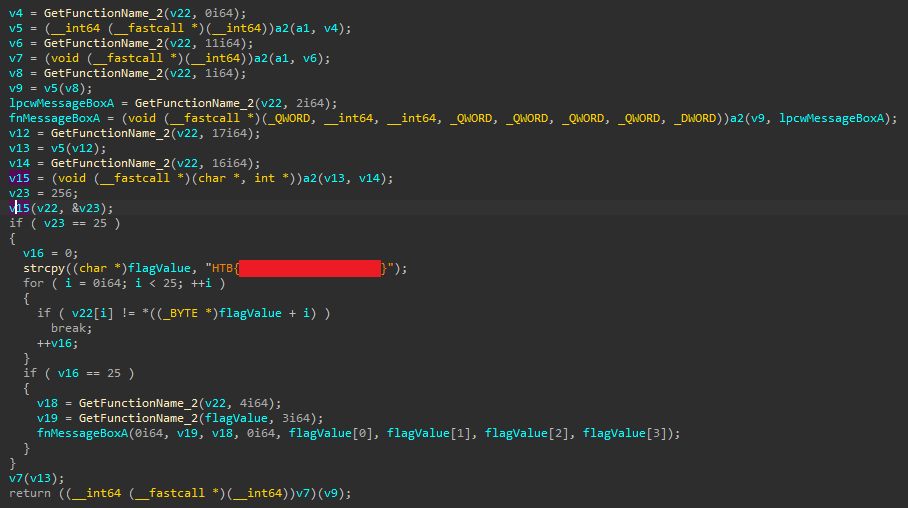
Then I opened it in IDA and saw that the decrypted code was also resolving more functions dynamically, although these function’s aren’t too important as the flag is visible in plaintext at this point.
The functions would open up a message box containing the flag value I think.
Lessons Learned
I spent much more time on this challenge than I should have. A lot of time was wasted on reversing the exact infection process and seeing what fields were being changed in the headers of the victim file. I should have focused on the decryption portion and the code surrounding that instead. All in all, I think for next time I should focus less on the details and more so on the “bigger picture” of what the application is doing.